Instead, security controls similar to digital banking should to be applied to APIs, and a“do not trust” approach should be adopted to provide a stronger and resilient future for APIs.
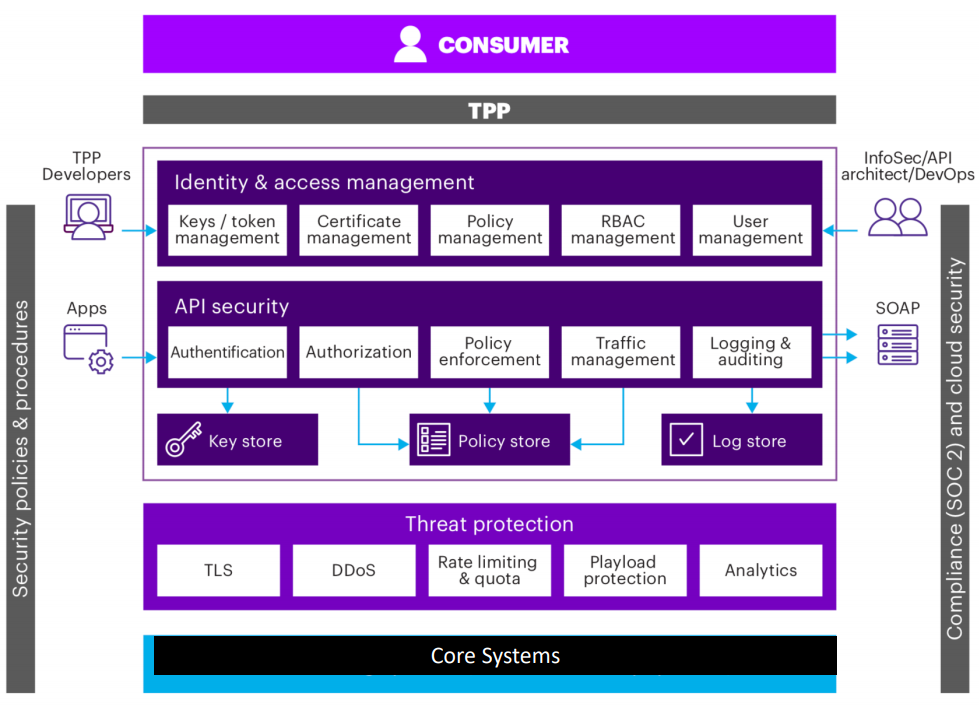
This security layer should address issues of:
- Access Control
- Threat Detection
- Confidentiality
- Integrity
Within this architecture, the design of APIs must take into account the need to protect against distributed denial of service (DDoS) attacks. Fortunately, this threat is also an opportunity. Since creating systems with open APIs represents a “greenfield” development for many organizations, it provides a one-off window of opportunity to do things right from start, by blocking attacks high up the stack and protecting the intelligence located on lower layers.
Authentication and Authorization
Authenticate licensed TPPs using the TPP certificate issued by a QTSP under PSD2 and check against revocation list. In addition to this, maintain a list of licensed TPPs gathered from the EBA Register.
Content Based Attacks
Protect against different types of content-based attacks such as malformed XML threats, malformed JSON threats, and malicious script injection threats.
Data Encryption
Use transport layer encryption such as TLS to secure the communication. Any sensitive message in the API needs to be protected using message/field level encryption.
Identity Tracking
User info and/or TPP ID should be logged for Identity tracking using policies within the flow.
Message Validation
Use Data Masking policies for hiding sensitive data when logged. A "validation before consumption" principle should be used to safeguard APIs.
Traffic Management
Use traffic management policies to prevent infrastructure getting overwhelmed. Implement throttling and rate limiting on the number of requests allowed for a TPP in a given time period.